Wave of cybersecurity breaches is no surprise to expert exposing online crime
Brian Krebs has been sent heroin and a wreath in an attempt to discredit and intimidate him but sees irresponsible hardware manufacturers as the real threat
Brian Krebs does not use heroin, but sometimes people send it to him anyway. The 43-year-old Alabama native writes Krebs on Security, a one-man operation focused on digital crime. His encyclopedic knowledge of the subject and his network of contacts has made his blog essential reading for anyone interested in cybercrime and a coveted lecturer at some of the biggest companies in the world. It has also made him some dangerous enemies hence the heroin, meant as a sinister, silencing message.
Looking back on a year in which Russian cyber-spies have been accused of meddling in the US election, Yahoo announced that 1bn email accounts were compromised and hackers used internet-connected devices including baby monitors, webcams and thermostats, to take down some of the worlds biggest websites, what surprises Krebs the most is that people are surprised at all.
The problem is cybercrime is easy, Krebs says. Too many individuals and organizations buy cheap hardware because they cant imagine the damage millions of slightly-too-stupid routers can do; most owners of the hijacked devices that participated in the attack that took down websites, including Netflix, Twitter, Reddit, CNN and PayPal, as well as the entire country of Liberia earlier this year never knew their property had been used to pull millions of computers offline.
Its cheap to make hardware that works, Krebs says. Its much more expensive to make sure it works only for you. There are companies that have zero interest in designing a secure device; they just cobble together software libraries.
When laypeople write to him, Krebs says, its often to beg for help. People get so frustrated and theyre scared and the clock is ticking and they dont know what to do, he says. They ask where do I go? Who do I turn to? Soon, he says, something will have to give.
Krebs was writing about a similar bug to the one Yahoo claims compromised 1bn user accounts as far back as 2012; for years hed warned readers about botnets like the one that took down the web across the eastern seaboard in October.
What shocked him, he said, was that people kept using Yahoo, and that the political establishment was somehow surprised that Russian hackers might want to see if they could impact the direction of our election. Of course they tried, Krebs says its cheap and you dont lose much by trying.
Krebs earns a living dragging the perpetrators of obscure and horrifying crimes into the light: before the Washington Post laid him off, his column Security Fix exposed Estonian cybercriminal Vladimir Tatin, whose domain-hosting business turned out to be a berth for child abusers and credit card thieves. Writing on his unshowy blog two years later, Krebs broke news of the notorious Stuxnet worm, a tool of corporate espionage capable of intruding on anyone who used Windows.
His subjects dont enjoy seeing their crimes written about, and sometimes they want to send him a message. In 2013, that message took the form of a gram of pure heroin taped to the back of a magazine.
That year, Krebs had earned the unwanted attention of a man calling himself The Fly, or Flycracker, later revealed to be a 26-year-old career thief named Sergey Vovnenko. Krebs tracked Vovnenko to a forum where he brokered the sale of credit card information, and found that Vovnenko was holding forth on a plan to damage Krebss reputation, maybe even land him in jail.
The plan was to have heroin delivered to Krebs, then to call the police. Krebs called the police first. The heroin came a few days after he gave his statement to law enforcement; he turned it over to the cops, and went to work finding who sent it.
Vovnenko fits a profile Krebs says applies to many in the world of information crime: young, arrogant and frankly sadistic, with a chip on his shoulder. Investigators are prone to boil credit card stealing operations and mass identity thefts to simple greed but often its more than that. These guys have such huge egos, he said. What are they after? How much is enough? You make 100 grand a month, is that not enough? Or do you really just enjoy fucking things up and attacking people or having power over people.
After Vovnenko failed to frame him, Krebs wrote about the experience in a blogpost, which the Guardian republished. He says he thinks the post embarrassed Vovnenko, who then sent Krebss wife a funereal flower arrangement.
He had it delivered to our house with a note to her, just to her, saying, Dear Jennifer, you married the wrong guy, but well always take care of you. Rest in peace, Brian. And at this point I want to know who this fucker is.
He found out: Vovnenko just like the people he stole from shared passwords between the administrator account on his identity theft forum, and the Gmail address he used to do his dirty work. Krebs learned that Vovnenko didnt trust his fiancee and had her every keystroke logged and secretly sent to the Gmail account; in those messages was every possible personal detail about Vovnenkos life.
Vovnenko lived in Naples, Italy. He had a son. He married his fiancee. He bought stolen Italian credit card information, printed and embossed credit cards on machines he owned himself, and cashed the cards out through high-end Italian retailers in the fashionable city, Krebs found.
Krebs decided to get in touch with Vovnenko. Running organized crime was one thing; a Ukrainian running an identity theft ring and printing stolen credit cards in the Camorras backyard was another. I just reached out to him and said, Hey, hows Italy? Hows your son Max? Krebs recalls. And he said Ahahaha, I wait for FBI.
I said: Its not the FBI you have to worry about.
Vovnenko fell afoul of Italian authorities and spent a while in what he called Naples worst prison in a letter of apology he wrote to Krebs. Krebs thinks Vovnenko was in a 12-step program; he also told his victim he forgave him for posting a picture and Vovnenkos address on Krebs on Security when Vovnenko was arrested.
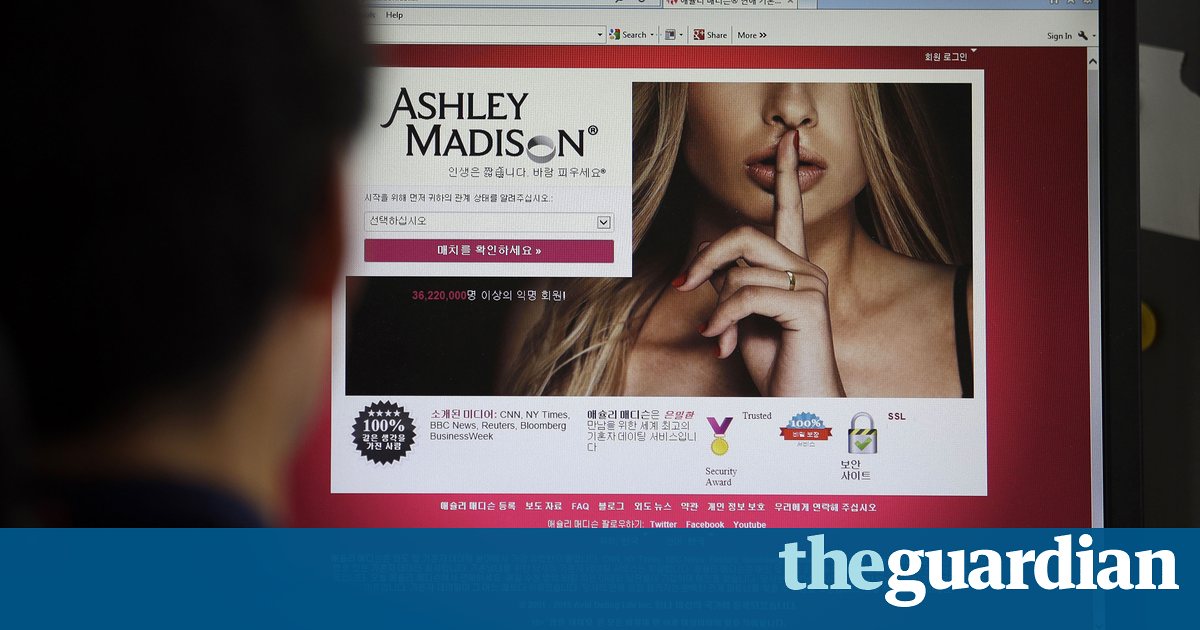
Criminal enterprise, especially with an eye to dominating or inflicting humiliation, tends to be the work of young men. Cybercrime is often very humiliating Krebs recalls the Ashley Madison hack, in which thieves used the data from the cheating spouses website to write extortion letters filled with details culled from social media another story Krebs first brought to light. Heres the number of the last guy who thought I was bluffing, they said. Call him and see if hes happy with how it turned out.
Like many security researchers, Krebs says the keys to avoiding cybercrime arent complicated. Identity theft has largely ceased to be a matter of targeting a specific person; the responsibility for preventing it lies with irresponsible hardware manufacturers who refuse to secure their devices with basic encryption. Hardware companies are struggling to reconcile the higher cost of securing devices with the danger to billions of users that comes with cheaping out on crucial parts. Meanwhile, its up to users to keep track of the basics.
Five things you can do to avoid digital criminals
Like most theft, cybercrime tends to follow the path of least resistance. Here are five online hygiene tips anyone can follow, for free, to make life harder for people looking for an easy way to steal your personal or financial information.
- Use multifactor authentication, a password plus a code or a question known to you. Googles authenticator app is a quick download and works easily with many services, including Amazon and Gmail. Its worth checking to see if theres a multifactor option every time a website asks you to fill out bank account or credit card information.
- Dont share passwords across websites. Almost everyone shares at least a couple of passwords. Dont. There are plenty of inexpensive password manager phone apps that can help you with this, notably the open-source Password Safe.
- Refuse to give up information whenever you can. Best Buy doesnt need your phone number. The more information you part with, the more can be used against you if the retailer is hacked.
- Check your bank balance regularly. Thieves often try for a small purchase to see if the card works before they go shopping; in particular, look for easy-to-resell items like gift cards and credits on online marketplaces.
- Close down services you dont use any more. Do you still have a Steam account from that one time you bought a PC game all your friends were talking about? Are you sure? Is it linked to a credit card you still use? These are the easiest ways for hackers to steal in bulk, and the one-off purchase you make on impulse is probably the one youll unthinkingly reuse your old password on, too.
Read more: https://www.theguardian.com/technology/2016/dec/23/cyber-security-breach-brian-krebs-crime